
Gaming Consortium
Unified identity, sanctions, age, and responsible gaming enforcement across multi-operator ecosystems without sharing PII.
Read more →Zekret Labs
A unified trust fabric providing verifiable identity, structured attestations, non-PII compliance-state intelligence, and governed AI augmentation.
Designed for banking, public-sector institutions, regulated gaming, enterprise governance, and digital asset oversight.

Core Value Prop
A unified trust infrastructure centered on identity integrity, compliance governance, and federated intelligence.
A privacy-preserving identity model enabling reusable, verifiable credentials without centralizing or exposing personal data.
Identity becomes reusable, non-PII, and consistently validated across institutional environments.
Deterministic compliance-state evaluation across all workflows, channels, and operating environments.
Compliance becomes a single, authoritative system of record—free from interpretive variance and operational fragmentation.
A governed intelligence layer delivering explainable, policy-constrained AI augmentation inside the institution’s own perimeter.
AI becomes safe to deploy in regulated environments: transparent, governed, and aligned to institutional obligations.
Industries
A trust infrastructure built for environments where identity, compliance, and governance determine operational integrity.
Products
A modular infrastructure stack that unifies identity governance, compliance intelligence, and AI-driven decisioning across high-assurance sectors.
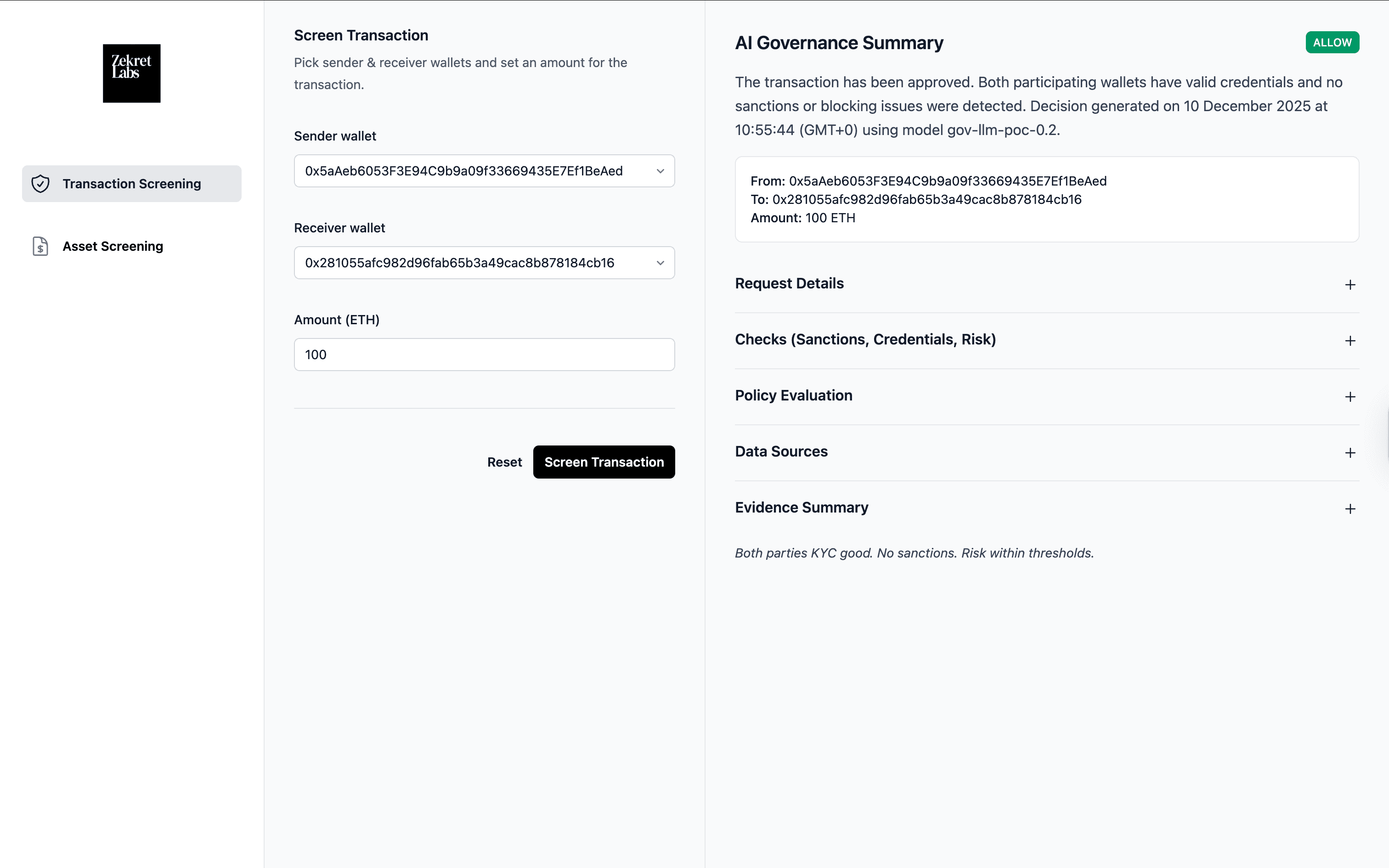
Architecture Overview
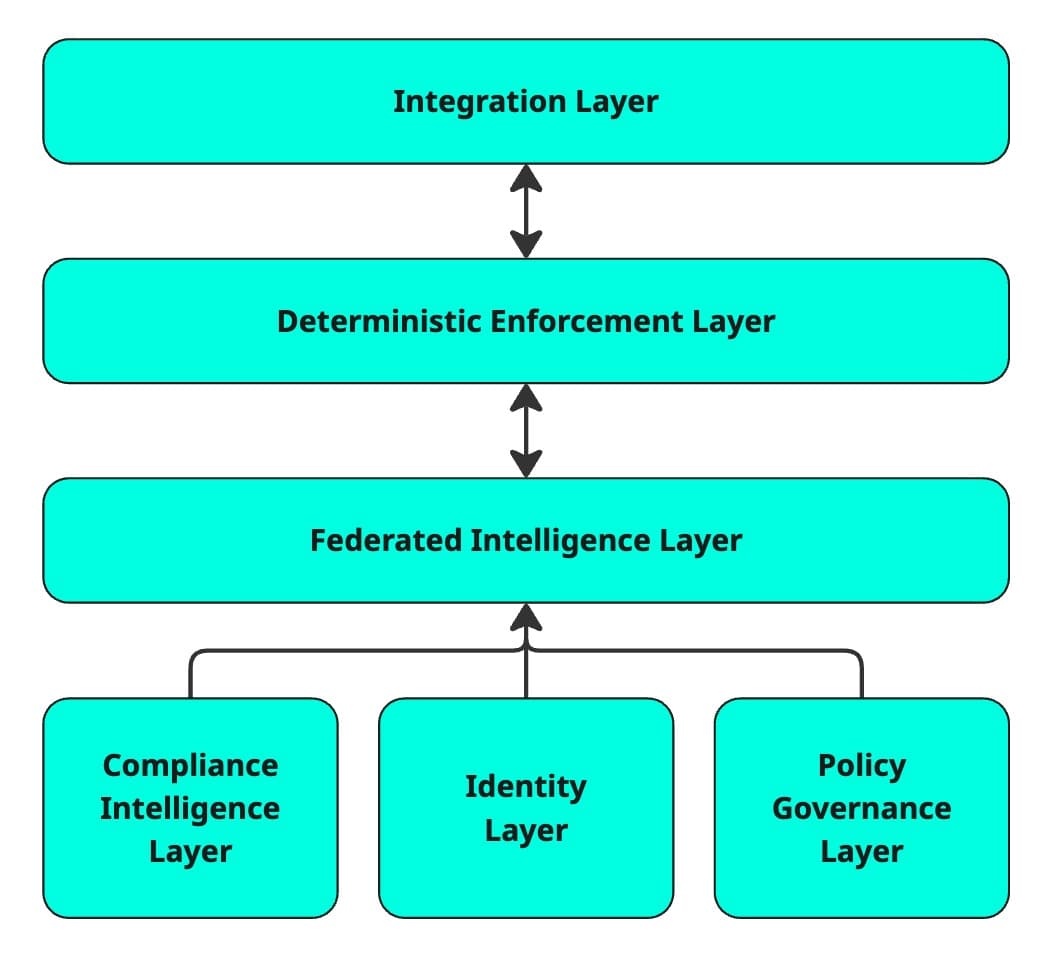
A vertically integrated trust fabric that spans identity, compliance intelligence, governance, federated AI, and deterministic enforcement.
Issuance, attestations, selective disclosure.
Sanctions, jurisdiction, behavioral signals, non-PII compliance-state.
Deterministic rules, version control, structured evaluation.
Local inference, explainability, policy-constrained outputs.
Consistent, auditable enforcement results.
SDKs, APIs, and gateway for enterprise and public-sector systems.
Deployment Models
Choose the hosting model that aligns with your compliance, sovereignty, and operational requirements.
Managed, isolated tenancy with rapid rollout.
Runs inside your cloud boundary with full data control.
Deploy within your data centers for strict residency needs.
Offline deployment for sovereign or classified environments.
Case studies
Proof points from regulated ecosystems where identity, compliance, and governance work together.

Unified identity, sanctions, age, and responsible gaming enforcement across multi-operator ecosystems without sharing PII.
Read more →
Reusable identity, sanctions intelligence, policy-bound eligibility, and explainable intelligence inside a bank’s VPC.
Read more →
Cross-agency eligibility verification without data sharing; deterministic rule enforcement; sovereign AI assistance.
Read more →
Deployment of Zekret as a sovereign trust substrate across an ecosystem requiring universal eligibility and policy governance.
Read more →Deploy trusted identity, deterministic compliance, and sovereign AI governance across your most critical operations.